Facebook started 2016 with the bold claim that it intends to eradicate phone numbers and replace web browsing, but the Social Network has a mountain to climb before Facebook Messenger becomes the centre of our online world.

That’s the stated intention of the Zuckerberg empire – to replace all our myriad internet communication systems with one interface.
Facebook claims that its Messenger app has been installed 800 million times, but at VisionMobile our latest research shows that those installations are very much concentrated into the lower end of the market.
If Facebook is going to recruit the shops, taxi companies and airlines it needs to make Messenger a one-stop internet shop it will need to get the app installed across the demographics before Microsoft (with Skype) steps in to take the cream.
[tweetable]Facebook has long known that the days of pokes and personal walls are fast disappearing[/tweetable], and has quite a history in struggling to adapt to whatever the future might bring. Facebook Gifts/Credits/Deals/Questions/Beacon haven’t lit up the future, so now the company is betting on messaging, and value-added messaging platforms.
Such platforms are proliferating in business. The bots that proliferate across Slack and Yahoo Messenger have turned those platforms into much more than messaging, but taking that functionality into the consumer sphere is much harder.
The medium is the Messenger
With that in mind, Facebook Messenger was forked from the main Facebook mobile app back in 2011, but messaging remained possible in the main app until 2014. These days, the Facebook app will notify you that a message has been received, but if you want to read that message then you’ll have to download and install Facebook’s new Trojan Horse.
That analogy isn’t perfect: the horse of Troy was disguised while Facebook has made no secret of its plan to migrate key internet functionality into the Messaging client. If Facebook can’t own the interface to your phone (it tried that), then it will own the interface to the internet, which the company believes will be Facebook Messenger.
The inspiration behind this idea isn’t hard to see. In China, where Facebook/Google/Twitter fears to tread, the competitive market created in their absence has driven huge innovation as companies strive to differentiate themselves with new features and functionality. Every month, 600 million Chinese are using Weixen, Tencent’s WeChat client, to book taxis, check into flights, play games, buy cinema tickets, make doctors’ appointments, and even manage bank accounts, all without touching the web browser.
[tweetable]In China, messaging has become the platform of choice for accessing a wide variety of services[/tweetable], and Facebook plans to replicate that model in the rest of the world – with it owning the messaging platform, obviously.
This process has already started with Facebook integrating Uber into its messaging platform. It’s worth noting that Uber isn’t integrated into the Facebook website, or the mobile client, but into the Facebook Messenger app.
And Uber is just the beginning. As David Marcus, Facebook’s vice president of messaging products, makes abundantly clear: “We can help you interact with businesses or services to buy items (and then buy more again), order rides, purchase airline tickets, and talk to customer service in truly frictionless and delightful ways” – and that’s before Facebook becomes your personal assistant, Facebook M.
“Facebook M” starts listening in to all your conversations to suggest ways it can make your life more, as they say in such circles, “delightful.”
The Facebook wall will be supplanted by the Custom Conversation, providing a personalised interface (colour, style, emojis) for every chat thread. The visual equivalent of a ring-back tone, customised for every caller, will enable you to decide how both sides of the conversation see their interface, unless the other side has other ideas.
Walled garden of Zuck
In Facebook’s brave new world, everything is done through Facebook Messenger, and Facebook takes control of the delivery channel, removing that irritating “Open in Web Browser” which takes so much control away from the Social Network.
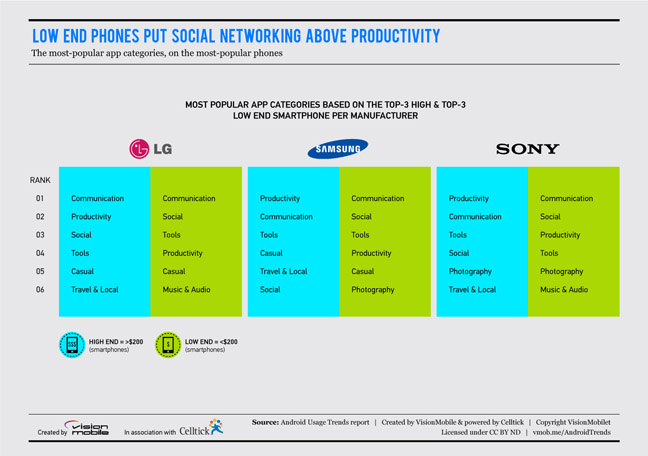
But that brave new world is predicated on the idea that people will install Facebook Messenger, rather than relying on the website, and email notifications, to stay in touch. Our research, in partnership with Celltick, looked at the top 10 applications installed on different handsets, and shows that while many low-end handsets do have Facebook Messenger installed, the application is almost invisible in handsets costing more than $200.
In high-end phones, Skype consistently rates top – well above the main Facebook application – and Facebook Messenger isn’t even in the top 10. In handsets costing less than $200, Facebook Messenger rates around four or five – a couple of positions below the main Facebook application, and very close to Skype.
What this means is that those who can’t, or won’t, invest more than $200 in a handset are happily installing Facebook Messenger, while those with a bit more disposable income are refusing to commit.
What it makes abundantly clear is the opportunity this presents to Microsoft. If messaging really is the future of mobile interaction, as Facebook seems to think, then Skype is perfectly positioned to grab the most important demographic.
If Microsoft were half as willing as Facebook to launch into value-added messaging, then it could make Skype into the messaging platform of the future, if indeed users really want such a platform at all.
You can read more in our free report, here (email address required.) ®


